In Part 1, we discussed how to train a monolingual tokenizer and merge it with a pretrained LLM’s tokenizer to form a multilingual tokenizer. In...
Enhancing the Apparel Shopping Experience with AI, Emoji-Aware OCR, and Snapchat’s Screenshop
Ever spotted someone in a photo wearing a cool shirt or some unique apparel and wondered where they got it? How much did it cost?...
Webinar: Path Traced Visuals in Unreal Engine
Integrate RTX into your own game and understand what ReSTIR means for the future of real-time lighting in this May 21 webinar. Integrate RTX into...
Develop Secure, Reliable Medical Apps with RAG and NVIDIA NeMo Guardrails
Imagine an application that can sift through mountains of patient data, intelligently searching and answering questions about diagnoses, health histories, and... Imagine an application that...
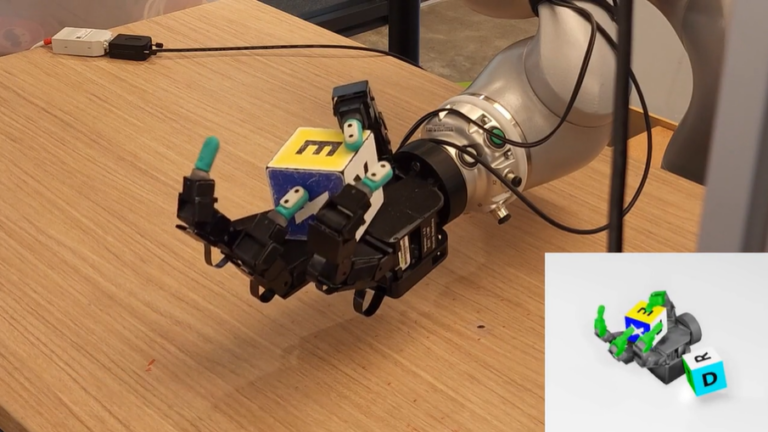
NVIDIA Presents New Robotics Research on Geometric Fabrics, Surgical Robots, and More at ICRA
During the IEEE International Conference on Robotics and Automation (ICRA) May 13-17 in Yokohama, Japan, many people will be discussing geometric fabrics. That... During the...